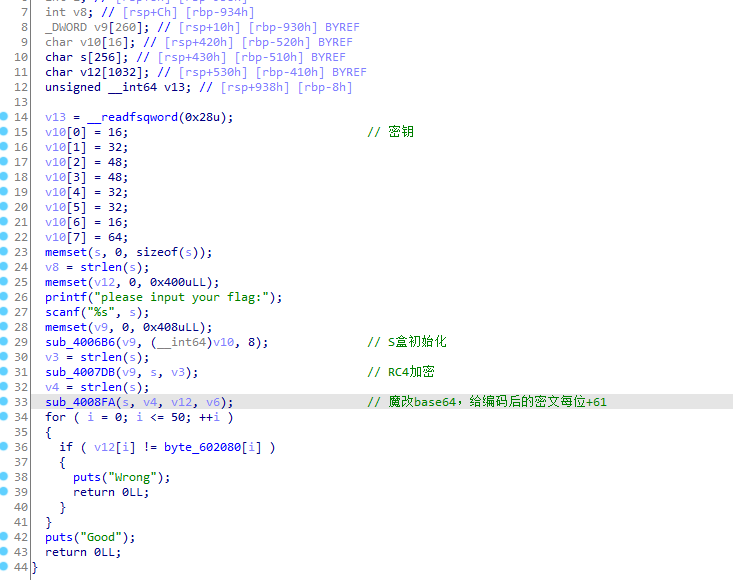
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| from Crypto.Cipher import ARC4
from binascii import unhexlify
v12 = [
0x5A, 0x60, 0x54, 0x7A, 0x7A, 0x54, 0x72, 0x44, 0x7C, 0x66,
0x51, 0x50, 0x5B, 0x5F, 0x56, 0x56, 0x4C, 0x7C, 0x79, 0x6E,
0x65, 0x55, 0x52, 0x79, 0x55, 0x6D, 0x46, 0x6B, 0x6C, 0x56,
0x4A, 0x67, 0x4C, 0x61, 0x73, 0x4A, 0x72, 0x6F, 0x5A, 0x70,
0x48, 0x52, 0x78, 0x49, 0x55, 0x6C, 0x48, 0x5C, 0x76, 0x5A,
0x45
]
binstring = ''
for i in range(len(v12)):
binstring += bin(v12[i] - 61)[2:].zfill(6)
print(binstring)
print(len(binstring))
s = []
for i in range(0, len(binstring), 8):
s.append(int(binstring[i:i+8], 2))
RC4_cipher = ''.join(hex(i)[2:].zfill(2) for i in s)
print(RC4_cipher)
key = ''.join(hex(i)[2:].zfill(2) for i in [16, 32, 48, 48, 32, 32, 16, 64])
RC4_cipher = unhexlify(RC4_cipher.encode())
key = unhexlify(key.encode())
rc4 = ARC4.new(key)
flag = rc4.decrypt(RC4_cipher)
print(flag)
|