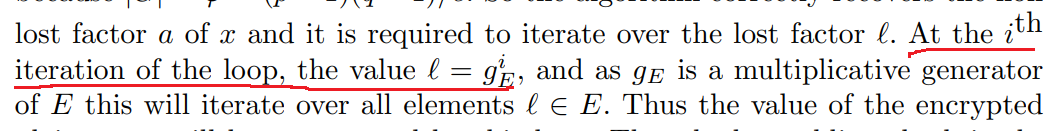large case 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from Crypto.Util.number import *from secret import e,messagedef pad (s ):if len (s)<3 *L:bytes (3 *L-len (s))return s128 assert isPrime(GCD(e,p-1 )) and isPrime(GCD(e,q-1 )) and isPrime(GCD(e,r-1 )) and e==GCD(e,p-1 )*GCD(e,q-1 )*GCD(e,r-1 )assert len (message)>L and len (message)<2 *Lassert b'SUSCTF' in messagepow (m,e,n)print (c)
根据$e==GCD(e,p-1)*GCD(e,q-1)*GCD(e,r-1)$,设$e = e_pe_qe_r$。
现在,我们求得了e,但gcd(e,(p-1)(q-1) (r-1)) = e,并不能直接解密,可以用AMM算法求解。
但这里根据官方题解用一个更快的方法。(算法来源:1059.pdf (iacr.org) )(稀里糊涂,英语水平有限,看不懂)
但满足如下条件:
由于该算法的时间复杂度为O(e),即与e成线性关系,因此我们可以通过缩短e来缩短时间。
根据题目中$len(message)>L\ and\ len(message)<2*L$,而通过$pad$函数可以发现,message的填充部分>1024bit。因此可以将n缩小为pq,e缩小为$e_pe_q$。
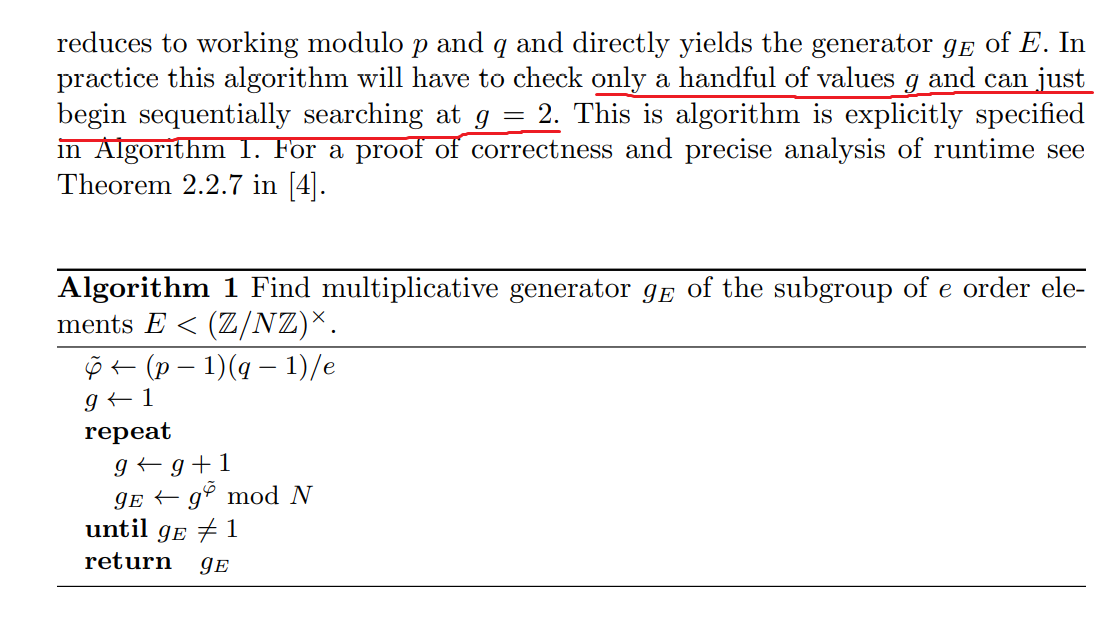
第一步:寻找$g_E$。
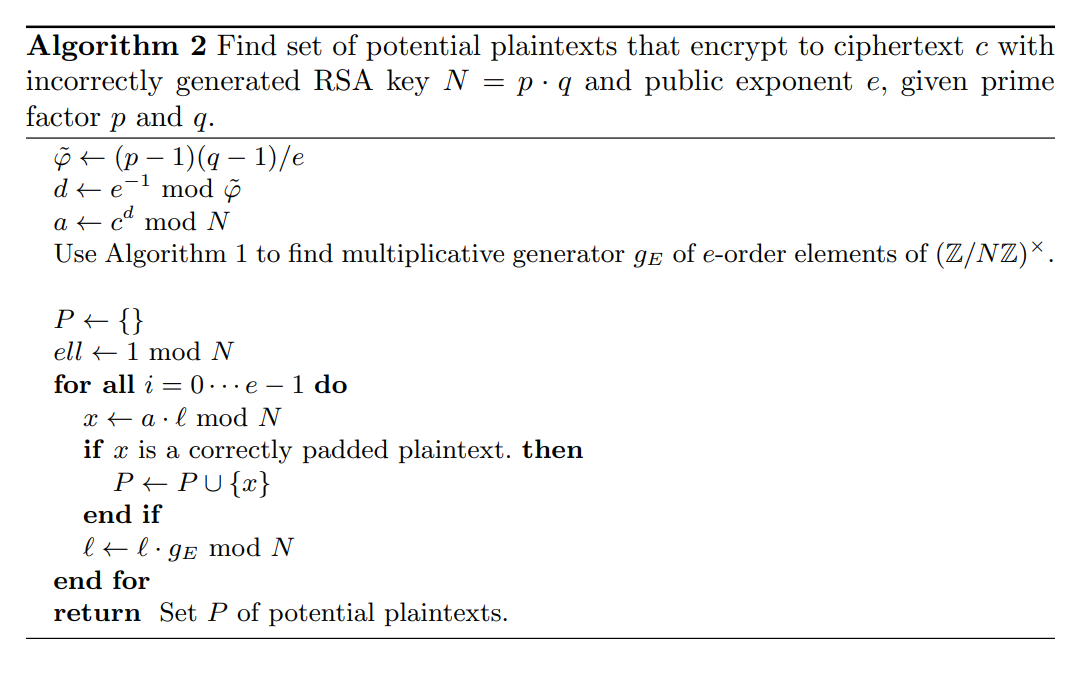
第二步:找符合的明文
其中的$l$为$l=g_E^i$。
代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 from Crypto.Util.number import *import primefacimport gmpy2import tqdm127846753573603084140032502367311687577517286192893830888210505400863747960458410091624928485398237221748639465569360357083610343901195273740653100259873512668015324620239720302434418836556626441491996755736644886234427063508445212117628827393696641594389475794455769831224080974098671804484986257952189021223 145855456487495382044171198958191111759614682359121667762539436558951453420409098978730659224765186993202647878416602503196995715156477020462357271957894750950465766809623184979464111968346235929375202282811814079958258215558862385475337911665725569669510022344713444067774094112542265293776098223712339100693 165967627827619421909025667485886197280531070386062799707570138462960892786375448755168117226002965841166040777799690060003514218907279202146293715568618421507166624010447447835500614000601643150187327886055136468260391127675012777934049855029499330117864969171026445847229725440665179150874362143944727374907 2832775557487418816663494645849097066925967799754895979829784499040437385450603537732862576495758207240632734290947928291961063611897822688909447511260639429367768479378599532712621774918733304857247099714044615691877995534173849302353620399896455615474093581673774297730056975663792651743809514320379189748228186812362112753688073161375690508818356712739795492736743994105438575736577194329751372142329306630950863097761601196849158280502041616545429586870751042908365507050717385205371671658706357669408813112610215766159761927196639404951251535622349916877296956767883165696947955379829079278948514755758174884809479690995427980775293393456403529481055942899970158049070109142310832516606657100119207595631431023336544432679282722485978175459551109374822024850128128796213791820270973849303929674648894135672365776376696816104314090776423931007123128977218361110636927878232444348690591774581974226318856099862175526133892 for ep in primefac.primefac(p-1 ):if ep>2 and pow (c%p,(p-1 )//ep,p)==1 :break for eq in primefac.primefac(q-1 ):if eq>2 and pow (c%q,(q-1 )//eq,q)==1 :break for er in primefac.primefac(r-1 ):if er>2 and pow (c%r,(r-1 )//er,r)==1 :break 1 )*(q-1 )pow (256 ,128 *e,n),n)%npow (c1,d1,n0)1 while 1 :1 pow (g,(p-1 )*(q-1 )//e0,n0)if gE != 1 :break pow (c0,d0,n0)for i in tqdm.tqdm(range (e0)):if b'SUSCTF' in m:print (flag)break
参考:
SUSCTF2022_official_wp/crypto at main · susers/SUSCTF2022_official_wp (github.com)
1059.pdf (iacr.org)
2022 SUSCTF SU Writeup | TEAM-SU
SUSCTF 2022 By W&M - W&M Team (wm-team.cn)
SUSCTF_Crypto_large case_复现_M3ng@L的博客-CSDN博客